The Malware Menace Understanding the Diverse World of Malware
Malware, or malicious software, poses a significant threat to individuals and organizations alike. Its various forms, from ransomware to spyware, are designed to infiltrate systems, steal data, and disrupt operations. This guide provides an in-depth look at the different types of malware you are most likely to encounter, along with real-world examples and actionable insights to fortify your defenses.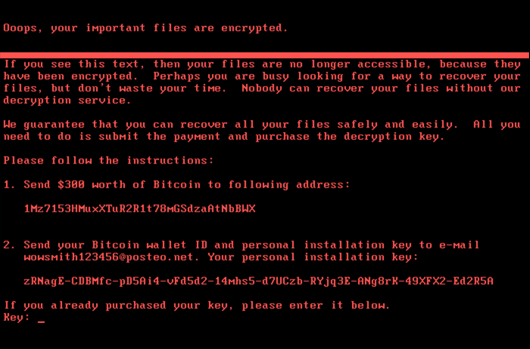
CrowdStrike offers comprehensive cybersecurity solutions designed to detect, prevent, and respond to these threats. Understanding the different types of malware is the first step in protecting your valuable data and maintaining business continuity.
Ransomware Holding Data Hostage: The Threat of
Ransomware is a particularly destructive type of malware that encrypts a victim's data, rendering it inaccessible until a ransom is paid. The attackers demand payment, typically in cryptocurrency, for the decryption key. However, there's no guarantee that paying the ransom will lead to the data's recovery, making this a high-stakes gamble.
A prime example is the RobbinHood ransomware attack on Baltimore, which crippled city operations for weeks and resulted in significant financial losses. The attack on Atlanta in 2018 highlights the recurring threat. Organizations must prioritize robust backup and recovery strategies and security awareness training to mitigate the risks associated with ransomware.
Fileless Malware Stealthy Attacks: The Rise of
Fileless malware operates without installing files, instead manipulating legitimate system tools like PowerShell or WMI to execute malicious code. This makes it harder to detect with traditional antivirus software because it uses existing system processes, often avoiding detection altogether.
The Astaroth campaign exemplifies fileless malware, leveraging legitimate Windows tools to download and execute malicious code solely in memory, making it nearly undetectable by standard security measures. This type of attack underscores the need for advanced threat detection capabilities.
Spyware The Silent Watchers: Understanding and its Impact
Spyware secretly collects user activity data, including passwords, payment information, and more, without the user's knowledge or consent. The damage extends beyond the initial data theft, often degrading performance and eroding productivity within an organization.
DarkHotel, which targeted business and government leaders through hotel Wi-Fi, is a striking example. The keyloggers installed on targeted systems captured sensitive information, emphasizing the need for secure network practices and endpoint security.
Adware The Annoying & Dangerous: Exploring and its Risks
Adware tracks user browsing activity to serve targeted advertisements. While seemingly harmless, it can compromise user privacy and expose sensitive information. Data collected by adware is often combined with other data to create detailed user profiles, which can be sold or shared with advertisers without user consent.
The Fireball adware, which infected hundreds of millions of devices in 2017, is a stark example. Beyond intrusive ads, it possessed the capability to execute code remotely, posing a significant threat to affected systems. Consider using community tools like CrowdInspect for additional security.
“Understanding the different types of malware is the first step in protecting your valuable data.
CrowdStrike
Trojans The Deceptive Disguise: Spotting and Preventing Trojan Attacks
Trojans disguise themselves as legitimate software or desirable content, tricking users into downloading and installing them. Once installed, a Trojan can grant attackers control over a victim's system, allowing them to steal data or launch further attacks.
Emotet, a sophisticated banking Trojan, remains a persistent threat, continually evolving and evading signature-based detection. The U.S. Department of Homeland Security has issued alerts regarding Emotet's widespread impact. Being aware of the latest indicators of compromise is key.
Worms Self-Replicating Threats: Understanding and Their Impact
Worms spread rapidly across networks by exploiting vulnerabilities in operating systems or software. They can gain access through various means, including backdoors, software vulnerabilities, or infected USB drives. Worms can be used to launch DDoS attacks, steal data, or deploy ransomware.
Stuxnet, developed by the US and Israeli intelligence forces, is a prime example of a worm. It targeted Iran's nuclear program. Although its primary function was sabotage, Stuxnet demonstrates the devastating potential of worms.
Want to stay up to date on recent adversary activities? Stop by the Counter Adversary Operations Blog for the latest research, trends, and insights on emerging cyber threats.
Further Resources
Deepen Your Knowledge
CrowdStrike 2025 Threat Hunting Report
Adversaries weaponize and target AI at scale. Download the report.
Start a Free Trial of CrowdStrike Falcon
Experience the power of comprehensive endpoint protection.
Counter Adversary Operations Blog
Learn more about the latest research, trends, and insights on emerging cyber threats.
Viruses The Contagious Code: Examining the Threat of
A virus is a piece of code that inserts itself into an application and executes when the application is run. Unlike Trojans or worms, a virus cannot execute or reproduce unless the application it has infected is running.
Understanding the distinctions between viruses, Trojans, and worms is crucial for effective cybersecurity. Many malware instances fit into multiple categories, for example, Stuxnet.
Rootkits The Hidden Hand: Unmasking the Threat of
Rootkits provide malicious actors with remote control of a victim's computer and full administrative privileges. They often hide themselves and other malware, making detection extremely difficult.
Zacinlo is a prime example, infecting systems through fake VPN apps and conducting a security sweep before engaging in click fraud. Understanding rootkits and bootkits are vital to securing systems.
“The malware landscape is constantly evolving. Staying informed and employing a layered approach to cybersecurity is crucial.
CrowdStrike
Keyloggers The Digital Spies: Unveiling the Dangers of
Keyloggers monitor user keystrokes, capturing sensitive data such as passwords and banking information. While they have legitimate uses, keyloggers are often employed for malicious purposes. Phishing, social engineering, and malicious downloads are typical entry points.
Olympic Vision is an example of a keylogger that targets businesses via spear-phishing. Being mindful of social engineering tactics can help protect businesses.
Bots/Botnets The Automated Army: Exploring Bots and Botnets
Bots are software applications that perform automated tasks on command. When numerous bots are connected, they form botnets, capable of launching large-scale attacks like DDoS attacks.
Protecting yourself involves staying informed about the latest threats and using reputable security solutions to keep your systems secure.
Conclusion Staying Ahead of the Curve: A Proactive Approach to Malware Prevention
The malware landscape is constantly evolving. Staying informed and employing a layered approach to cybersecurity is crucial. This includes implementing robust endpoint protection, user education, and regular security audits.
By understanding the various types of malware, their methods of operation, and the latest preventative measures, organizations can significantly reduce their risk and protect their valuable assets. CrowdStrike provides comprehensive solutions to address these threats. Contact us today for a free trial or to learn more about how CrowdStrike can help you secure your business.