Malware Navigating the Complex World of
Malware, or malicious software, encompasses a broad range of threats designed to infiltrate and damage computer systems. Understanding the different types of malware is crucial for effective cybersecurity. This guide provides a detailed look at common malware types, their methods, and real-world examples to help you recognize and defend against these threats.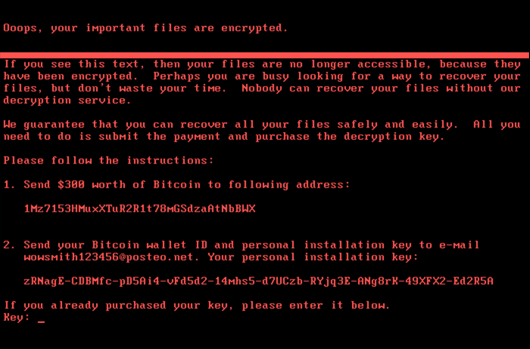
This guide delves into the most prevalent types of malware, examining their functionality and impact. We'll explore examples of each to illustrate the diverse ways malware can compromise systems and the critical importance of robust cybersecurity measures.
Ransomware : Holding Data Hostage
Ransomware is a particularly destructive type of malware that encrypts a victim's data, rendering it inaccessible until a ransom is paid. The attackers demand payment, usually in cryptocurrency, for the decryption key.
The consequences of a ransomware attack can be devastating, causing significant operational disruptions, financial losses, and reputational damage.
Real-World Example: The city of Baltimore fell victim to RobbinHood ransomware, which halted city services for weeks, costing over $18 million. Similar attacks have impacted other cities and organizations.
Fileless Malware : Stealthy and Silent Attacks
Fileless malware operates without installing files, instead using existing system tools like PowerShell or WMI to execute malicious code. Its stealthy nature makes it difficult for traditional antivirus software to detect.
This approach allows attackers to remain undetected for extended periods, increasing the potential for data theft and damage.
Real-World Example: Astaroth, a fileless malware campaign, used .LNK shortcuts to launch malicious code through legitimate Windows tools, stealing credentials and uploading them to a remote server.
Spyware : The Silent Collector
Spyware collects user data, including passwords, financial information, and browsing activity, without their consent or knowledge. This data can be used for identity theft, financial fraud, or corporate espionage.
Spyware can affect individuals and organizations and compromise privacy, productivity, and security.
Real-World Example: DarkHotel, targeting business and government leaders, used spyware and keyloggers to steal sensitive information via hotel Wi-Fi networks.
Adware : Annoying but Potentially Dangerous
Adware tracks user activity to serve targeted advertisements. While often considered a nuisance, adware can pose a security risk by tracking browsing habits.
The collected data can be used to create detailed user profiles, which can be shared or sold to advertisers without consent, compromising privacy.
Real-World Example: Fireball adware infected 250 million devices, hijacking browsers and potentially allowing remote code execution.
“Ransomware can be devastating, causing significant operational disruptions and financial losses.
CrowdStrike Research
Trojans : Disguise and Deception
Trojans masquerade as legitimate software or files to trick users into downloading and installing them. Once installed, they can grant attackers control over the victim's system, enabling them to steal data, install further malware, or launch other malicious activities.
These can be distributed through various means, including malicious downloads, phishing emails, and compromised software.
Real-World Example: Emotet, a sophisticated banking Trojan, is hard to detect and has caused significant damage, prompting alerts from the US Department of Homeland Security.
Worms : The Self-Replicating Threat
Worms are self-replicating malware that spread across networks by exploiting system vulnerabilities. Unlike viruses, they do not require a host file to execute.
Worms can cause significant network disruption and data breaches.
Real-World Example: Stuxnet, believed to be developed by the US and Israeli intelligence, targeted Iran's nuclear program through a flash drive, causing operational disruptions.
Protect Yourself
Stay vigilant and secure!
Download CrowdInspect
Download a free community tool to help you alert you to the presence of potential malware are on your computer.
Explore CrowdStrike Falcon
Learn more about CrowdStrike's proactive approach to cybersecurity and threat detection.
Viruses : The Embedded Threat
Viruses insert themselves into applications and execute when the application is run. They require a host application to function, setting them apart from worms, which self-replicate, and Trojans, which masquerade as legitimate files.
Viruses can be used for data theft, DDoS attacks, or ransomware.
Viruses are a dangerous threat to data security and operational integrity.
Rootkits : Concealing Malicious Activities
Rootkits provide attackers with remote control and administrative privileges over a victim's computer. They can hide the presence of other malware and facilitate unauthorized access and data theft.
Rootkits often employ stealth techniques to avoid detection.
Real-World Example: Zacinlo, a rootkit, installs through fake VPN apps and conducts activity to evade behavioral analysis.
“Fileless malware attacks are stealthy and can be up to ten times more successful than traditional malware attacks.
Cybersecurity Expert
Keyloggers : Capturing Every Keystroke
Keyloggers monitor user activity, capturing keystrokes to steal passwords, financial information, and other sensitive data. While keyloggers have legitimate uses, such as monitoring employee activity, they are often used for malicious purposes.
They can compromise privacy and security.
Real-World Example: Olympic Vision targeted businessmen for business email compromise attacks by using keyloggers.
Bots/Botnets : Automated Attacks at Scale
Bots are software applications that automate tasks on command. Botnets are networks of compromised computers (bots) controlled by a single attacker, often used to launch distributed denial-of-service (DDoS) attacks or spread malware.
Botnets represent a significant security threat due to their ability to scale attacks.
Understanding botnet tactics is crucial for recognizing and mitigating the impact of large-scale attacks.
Conclusion Staying Ahead of the Malware Game
The malware landscape is constantly evolving, with new threats emerging regularly. By staying informed about the different types of malware, their tactics, and real-world examples, you can better protect your systems and data.
Implementing strong security measures, including regular software updates, robust antivirus solutions, and employee education, is essential for mitigating the risks of malware attacks.
For the latest research, trends, and insights on emerging cyber threats, visit the Counter Adversary Operations Blog.