Phishing The Growing Threat of Attacks
Phishing attacks are a persistent threat to individuals and organizations alike. These attacks leverage deception to steal sensitive information, such as login credentials and financial data. Modern phishing attempts often mimic legitimate communications from well-known brands, making them difficult to spot.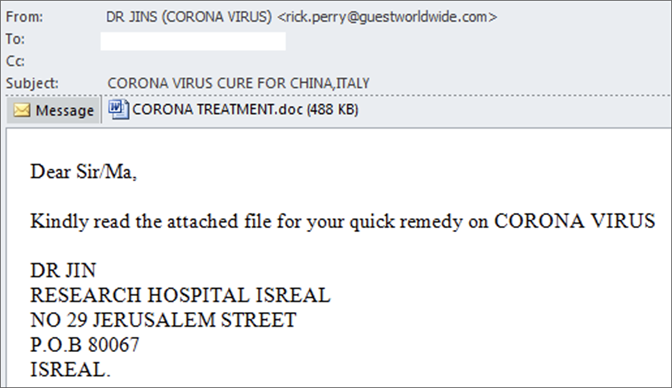
Unlike mass phishing campaigns, spear phishing attacks target specific individuals or groups within an organization. This refined approach often involves extensive research, increasing the likelihood of a successful breach and potentially leading to significant financial or reputational damage.
Phishing vs. Spear Phishing Key Differences and Attack Strategies
Phishing is a numbers game. Attackers cast a wide net, sending generic emails, texts, or messages to a large audience. These messages rarely use the recipient's name and rely on the recipient clicking a malicious link or downloading a harmful attachment.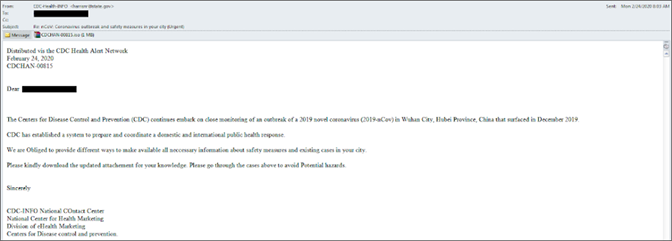
Spear Phishing is highly targeted. Attackers conduct research to personalize their attacks, often focusing on individuals within a specific company or industry. These attacks may include specific details that make the message appear legitimate, increasing the likelihood of a user taking the bait. Spear phishing can be the initial stage of a more sophisticated attack, such as an advanced persistent threat (APT).
Spear Phishing Real-World Examples
Attackers might impersonate an executive, requesting urgent wire transfers or access to sensitive data. This type of attack leverages social engineering, creating a sense of urgency to manipulate victims into acting quickly without thinking.
Another example involves emails pretending to be from the IT department, asking employees to reset their passwords. The email directs users to a fake login page that captures their credentials, which are then used to gain access to the company's network.
“Spear phishing attacks are at least as personalized as a typical corporate marketing campaign.
CrowdStrike
Explore CrowdStrike's Comprehensive Protection
Discover how our solutions can protect your organization from evolving phishing threats.
Threat Intelligence
Stay ahead of attackers with real-time threat intelligence. Understand the latest phishing tactics and the threat actors behind them.
Endpoint Detection and Response (EDR)
Detect and respond to threats on your endpoints with advanced behavioral analysis and machine learning.
Incident Response
Get expert help to rapidly investigate, contain, and remediate phishing attacks and breaches.
Protecting Yourself Essential Steps to Combat Phishing and Spear Phishing
Implement security awareness training to educate employees about the various types of phishing attacks and how to identify them. Regular training helps employees stay vigilant.
Conduct phishing simulations within your company to test employee awareness and assess the effectiveness of your security training. These simulations provide a safe environment for employees to practice identifying and reporting phishing attempts.
Ensure that remote services, VPNs, and multi-factor authentication (MFA) solutions are fully patched, properly configured, and integrated. Update software regularly to close vulnerabilities.
Use an anti-spam filter to automatically move phishing emails to your junk folder, reducing exposure to malicious content. Employ anti-virus software to scan devices to prevent, detect, and remove malware.
Validate URLs before clicking on links and never reply to spam emails. Responding to phishing emails confirms to attackers that your email address is active.
Consider implementing advanced security solutions that detect and respond to threats in real-time. CrowdStrike offers comprehensive protection against phishing and spear phishing attacks, including threat intelligence, endpoint detection and response, and incident response services.
CrowdStrike How Can Help
CrowdStrike provides a multi-layered approach to defend against phishing and spear phishing attacks. Our solutions use advanced threat intelligence, behavioral analysis, and machine learning to detect and prevent these sophisticated threats.
With CrowdStrike, you gain visibility into your endpoints, network, and cloud environments, allowing you to quickly identify and respond to threats. Our platform provides proactive protection, real-time threat detection, and rapid incident response capabilities.
Protect your organization with CrowdStrike. Start your free trial today.