What is Phishing? Understanding the Threat
Phishing emails are deceptive messages designed to steal your sensitive information, such as usernames, passwords, credit card details, and Social Security numbers. These fraudulent emails often masquerade as legitimate communications from trusted sources like banks, online retailers, or even colleagues.
The effectiveness of phishing lies in the exploitation of human psychology. Cybercriminals use social engineering tactics to create a sense of urgency, fear, or excitement. They mimic trustworthy sources with official logos, email addresses, and professional language to trick you into taking immediate action without considering the consequences. Knowing how to recognize a phishing email is crucial for protecting yourself online.
Phishing Common Techniques Used in Attacks
Phishing attacks employ various techniques to compromise your security.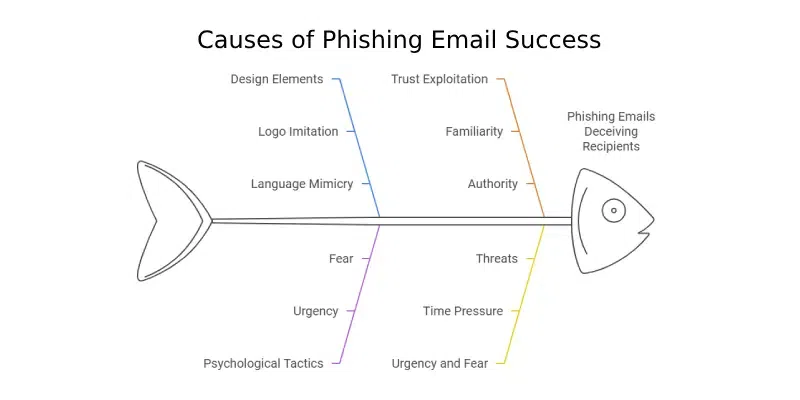
Email Spoofing: Attackers forge the sender's address to make emails appear to come from a legitimate source. This creates a false sense of trust.
Social Engineering: Phishers use social engineering tactics to manipulate you into divulging personal information. This might involve impersonating someone you trust or exploiting your emotions.
Malware Delivery: Phishing emails often contain malicious attachments or links that, when clicked, download malware onto your device. This malware can then steal your data or take control of your system.
Recognizing Key Indicators of Phishing Emails
Several key indicators can help you easily identify phishing emails:
1. Check the Email Address: Phishers often disguise their real email addresses to appear legitimate. Look for subtle variations in the sender's address. Legitimate emails come from known domains (e.g., support@amazon.com). Phishing attempts use unusual domains (e.g., amaz0n.com - note the zero instead of an 'o') or misspellings.
2. Suspicious or Generic Greeting: Phishing emails often use generic greetings like "Dear Customer" or "Dear User" because they don't have your actual name. Legitimate companies address you by name (e.g., "Dear John Doe"). Beware of generic greetings or misspellings in the salutation.
3. Sense of Urgency or Threat: Phishing emails often create a sense of urgency or fear to prompt quick action. They might threaten to lock your account unless you act immediately. Legitimate companies rarely pressure you for immediate action. Any email demanding immediate action to avoid penalties is highly suspicious.
4. Suspicious Links or Attachments: Phishing emails often include suspicious links or attachments designed to install malware. Hover over links to check the destination URL. Legitimate emails link to official websites (e.g., amazon.com). Phishing attempts redirect to malicious sites. Example: a link that looks like amazon.com but redirects to a different site.
5. Grammar and Spelling Mistakes: Many phishing emails contain noticeable spelling or grammatical errors. Legitimate emails from reputable companies are proofread. Phishing emails may have awkward phrasing, incorrect spelling, or missing punctuation.
6. Unsolicited Requests for Personal Information: Phishing emails often ask you to provide sensitive information (login credentials, credit card details, or personal data). No reputable company will ask for sensitive information via email. Beware of emails requesting you to confirm your login, PIN, or Social Security number.
7. Too Good to Be True Offers: If an email promises something unrealistic (large sum of money, unbelievable discounts), it's likely phishing. Phishers use attractive offers to lure you into clicking malicious links. Legitimate offers are reasonable and clearly explained. Offers that sound too generous are common in phishing emails.
Advanced How to Spot a Phishing Email: Techniques
For advanced users, further methods exist to identify phishing attempts:
1. Examine the Email Header: Analyze the email header for information about the sender and the message's path. Check the Return-Path: This field indicates where the email came from. If the domain doesn't match the sender, it's likely a phishing attempt. Check Authentication Results: Look for SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) results to verify the email's source.
2. Use Anti-Phishing Tools and Filters: Most email providers (Gmail, Outlook, Yahoo) have built-in spam filters to identify phishing. Tools like PhishTool or Email Verification Services also help validate the sender and authenticity.
3. Verify Through Official Channels: If an email from a bank, service, or friend seems suspicious, verify it through official channels. Do not click links in the email; instead, go to the official website directly and log in to your account.
“Phishing exploits human psychology by creating urgency and fear to manipulate users into taking immediate action.
Security Expert
Interactive Security Measures
Enhance your protection with these resources:
Phishing Quiz
Test your skills in identifying phishing attempts with our interactive quiz.
Report Phishing
Learn how to report phishing emails to help protect yourself and others.
Real-World Examples of Phishing Emails
Here are two examples of phishing emails:
Example 1: Subject: "Action Required: Secure Your Account Now"
Suspicious Email Address: Often spoofs a legitimate company name.
Suspicious Links: Links redirect to a website with a domain name similar to the legitimate one.
Urgency: Creates a sense of urgency, claiming immediate action is needed to prevent account lockout.
Call to Action: Clicking the link requests your username, password, and sometimes your Social Security number.
Example 2: Subject: "You've Won a Free iPhone! Claim Your Prize Now!"
Suspicious Email Address: Could be from a fake or random email.
Too Good to Be True: Offers an iPhone for free, without explanation.
Suspicious Links: Directs to an unfamiliar site requesting personal details (credit card information).
No Contact Info: Lacks physical address, phone number, or customer service information.
Conclusion Protect Yourself from Phishing Attacks
Recognizing phishing emails is critical for your online security. By staying vigilant and carefully examining suspicious emails, you can significantly reduce your risk of falling victim to phishing scams.
For beginners, focus on obvious signs: misspelled domain names, poor grammar, and unsolicited requests for sensitive information. Advanced users can leverage tools like header analysis and email verification services.
Always proceed with caution when dealing with suspicious emails. If in doubt, verify the message through official channels. By knowing how to identify and spot phishing emails, you can protect yourself from online fraud and identity theft.