Overview Decoding the 'I RECORDED YOU' Scam: What You Need to Know
The internet has unfortunately become a playground for cybercriminals. Email, in particular, is a prime target for malicious activities. Among the most prevalent threats is the 'I RECORDED YOU' extortion scam—a sophisticated attempt to exploit your fears and extract money. This article will unravel the intricacies of this scam, arming you with the knowledge to protect yourself.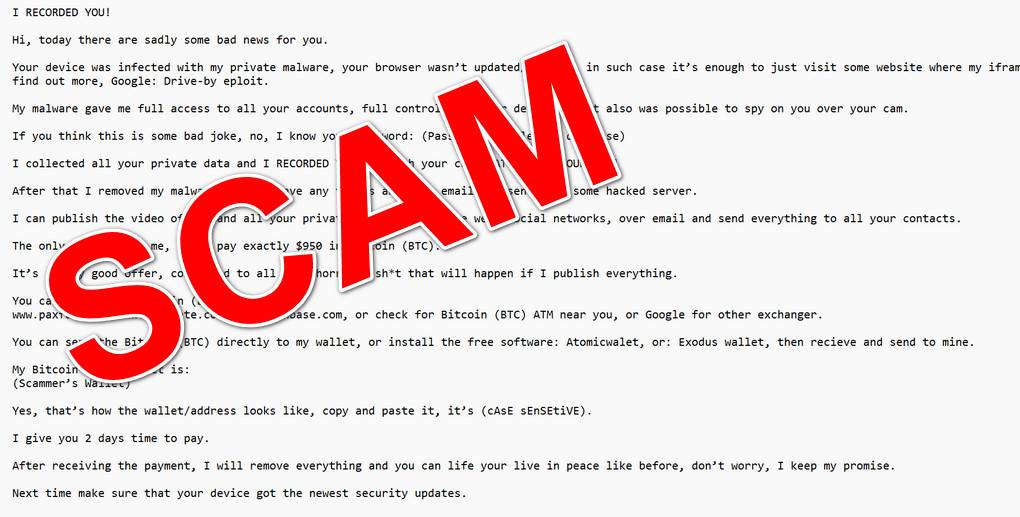
This email-based sextortion scam, which has circulated since at least 2017, leverages fear and intimidation to coerce victims into paying a ransom. The attackers claim to have recorded explicit videos and threaten to release them unless a payment is made, typically in Bitcoin. Understanding this threat and how to respond is crucial.
How It Works The Anatomy of an 'I RECORDED YOU' Scam Email
The scam operates through a few key stages, designed to maximize its impact. The email usually starts by claiming that the recipient's device was infected with malware. This malware, the scammers claim, gives them complete control over the device, including access to the webcam.
The core threat involves a fabricated claim of having recorded compromising videos, often showing the recipient engaging in private activities. To add a veneer of legitimacy, the emails may include a password that was previously exposed in a data breach. The actual passwords are often sourced from old, public data breaches.
The scammers then threaten to release these videos to the recipient's contacts if a ransom isn't paid promptly. The payment is almost always demanded in Bitcoin, making the transaction difficult to trace.
Crafting the Emails The Tactics Behind the 'I RECORDED YOU' Email Campaign
Scammers acquire vast lists of email addresses and leaked passwords from dark web markets or hacker forums. These credentials form the foundation of their operation.
The emails themselves are meticulously crafted to elicit fear, embarrassment, and a sense of urgency. They commonly include: claims of malware infection, access to your webcam, threats to expose compromising content, demands for Bitcoin, and often, an old password to appear legitimate.
Delivery Methods How the Scam Emails Reach You
The scam emails are sent from addresses that are spoofed to appear legitimate. Spoofing tricks some recipients into believing the email is from a real company or person, thus adding to the authenticity.
The 'from' name may match your name to further boost credibility. Scammers will often send emails in bulk. They target as many recipients as possible, understanding that only a small percentage will fall for the scam. Mass distribution is key to their success.
“Do not panic; the threats are a bluff.
Cybersecurity Expert
Take Action: Essential Steps
Protect yourself and your digital life with these immediate actions:
Report the Email
Report the scam email to your email provider and the IC3.
Strengthen Passwords
Change your passwords and enable 2FA.
Stay Informed
Educate yourself about online scams and stay vigilant.
Payment & Threats The Role of Bitcoin and Follow-Up Threats
Ransom payments are almost exclusively demanded in Bitcoin, allowing anonymity. Bitcoin enables the criminals to remain hidden and untraceable.
If the initial email doesn't work, scammers send follow-up emails, making increasingly aggressive threats. The demands for money may increase, sometimes doubling or tripling the original amount. The scammer's purpose is to frighten those who may have initially dismissed the first email.
The key point to remember: The scammers never possess compromising videos or access to your accounts. The entire premise is a fabrication.
Who Is Behind It? Unmasking the Perpetrators of the 'I RECORDED YOU' Scam
The 'I RECORDED YOU' scam originates from cybercriminal groups operating in West Africa, Russia, and Eastern Europe. Individual identities are rarely known because the scam is run through distributed networks of hackers utilizing encrypted communications.
These groups tend to operate internationally, making arrests extremely difficult. They maintain anonymity through encryption and Bitcoin. They also share information and email templates to bolster effectiveness. English-speaking countries are commonly targeted. The ability to hide behind the internet and Bitcoin wallets allows these scams to thrive.
Sextortion scams pose a major challenge for law enforcement and cybersecurity experts. These scams will likely continue unabated until greater international cooperation emerges.
What to Do If You Receive the 'I RECORDED YOU' Scam Email: Your Action Plan
Do not panic or submit payment. The scammers prey on your fear. Remain calm; understand the sender does not possess any compromising footage of you. The threats are empty. Paying the ransom will likely result in further demands and zero actual videos.
Report the email. Forward the email to your email provider's abuse team and report it as a phishing scam to platforms like Gmail or Outlook. Also, report the incident to the FBI's Internet Crime Complaint Center (IC3) to help in enforcement.
Reset passwords and enable 2FA. Change your passwords, especially for your email and financial accounts, and enable two-factor authentication (2FA) wherever possible.